Imagine waking up to find your bank account drained, your identity stolen, and your private medical history circulating online—all because a company you trusted lost control of your data. Sadly, this isn’t dystopian fiction. It’s a routine news story.
From Equifax to Facebook, from hospitals to dating apps, data breaches are no longer exceptional—they are systemic failures of digital infrastructure. But the real threat is deeper: when data leaks occur, trust collapses, reputations erode, and ethical accountability often vanishes into legal grey zones. This article explores how breaches happen, why they persist, and what must change to make digital trust real again.
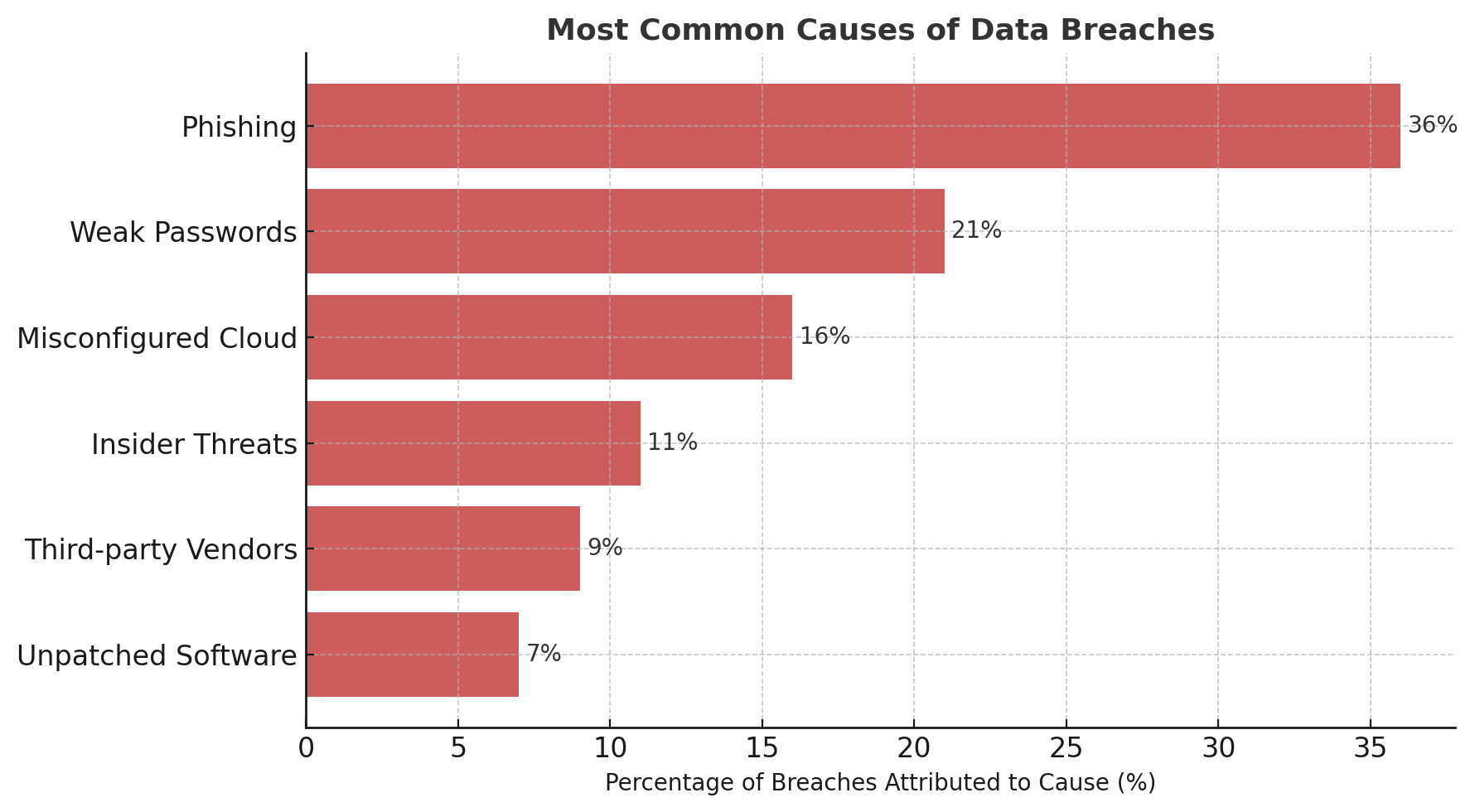
🧨 How Do Breaches Happen?
1. Phishing & Social Engineering
Hackers rarely "hack." They ask politely—by tricking someone into clicking a malicious link or entering credentials. These tactics bypass firewalls by targeting the weakest point: humans.
2. Weak Authentication
Reusing passwords, skipping MFA (multi-factor authentication), or relying on default credentials is a recipe for disaster—yet remains rampant across industries.
3. Misconfigured Cloud Storage
Exposed Amazon S3 buckets or unsecured databases are goldmines for attackers. These missteps often happen due to lack of cloud literacy among IT teams or overlooked defaults.
4. Third-party & Supply Chain Vulnerabilities
The 2020 SolarWinds breach affected thousands—not because the company was attacked directly, but because one of its vendors was compromised.
5. Insider Threats
Sometimes, it’s not the hackers—it’s your own employees. Whether malicious or accidental, insiders can leak, steal, or mishandle sensitive data with devastating consequences.
⚖️ Ethical and Legal Dilemmas
-
Who owns the breach? When a company leaks user data, is it a technical failure, or a moral one?
-
Is consent meaningful? Most users "agree" to data use via unread Terms of Service. But should that waive liability?
-
When should the public be told? Many firms delay breach notifications to protect stock prices, at the expense of user safety.
Data privacy laws like GDPR and CCPA attempt to create standards. Yet enforcement is inconsistent, and fines rarely match the damage caused.
🧩 Real-World Case: The Equifax Breach
In 2017, Equifax lost the personal data of 147 million people—including Social Security numbers and credit data. Why? A single unpatched Apache server vulnerability. The company failed to disclose the breach for weeks. Eventually, Equifax paid a $700M fine—but no executives faced criminal charges.
🧠 What’s the takeaway?
-
Poor patch management
-
Delayed disclosure
-
Lack of executive accountability
The system didn't fail. It worked exactly as it was built—to protect corporate assets, not consumer data.
🛡️ What Can Be Done?
For Organizations:
-
Zero-trust architecture: Assume no system or user is inherently safe
-
Regular audits and patch cycles
-
Third-party risk assessments
-
Incident response plans with legal + PR readiness
For Lawmakers:
-
Mandated breach disclosure timelines
-
Criminal penalties for willful negligence
-
Data ethics training for executives
-
Support for privacy-by-design development
For Individuals:
-
Use password managers + MFA
-
Don’t reuse passwords across services
-
Monitor credit and identity regularly
-
Think critically before sharing data online
🔮 Conclusion: Breaches Are Inevitable—Negligence Is Not
We cannot design a digital world without risk. But we can choose how we anticipate, respond, and compensate for failure. The true cost of a breach isn’t just financial—it’s moral, relational, and societal.
As more of our identities move online, the need for ethical data stewardship becomes not just a business imperative, but a civil one.
📰 Recent News & My Perspective
Below are some of the most alarming recent incidents and trends — followed by my personal view (as the author) on where things are heading.
📢 Recent Incidents & Trends (2025)
-
A massive credential leak surfaced: around 16 billion login credentials across various services exposed in multiple datasets. Many were new leaks, not just recycled old ones.
-
The New York Blood Center was breached: ~194,000 individuals had names, Social Security numbers, driver’s license numbers, banking data (for those on direct deposit), and medical info exposed.
-
Allianz Life (U.S.) confirmed a breach impacting the majority of its 1.4 million U.S. customers. The vulnerability reportedly exploited a third-party cloud system via social engineering.
-
Hackers claimed 1.5 billion Salesforce records were stolen across ~760 companies, targeting fields like Contact, Account, Opportunity, etc.
-
The Tea app (a dating advice / women’s safe space app) suffered multiple leaks: 72,000 images (IDs, selfies) plus ~1.1 million private messages containing sensitive and intimate content.
-
A high-impact ransomware attack on Collins Aerospace disrupted airport check-in and baggage systems across Europe, affecting travel operations.
-
The St. Paul (Minnesota) cyberattack escalated to a state of emergency, with the National Guard deployed after core city systems (payments, internal apps) were compromised. The attackers publicly released 43 GB of stolen data after the city refused to pay ransom.
These episodes show that breaches are now multifaceted: targeting infrastructure, third parties, software-as-a-service platforms, even city services. It’s not just data theft — it’s about disrupting trust, operations, and civic life.
🧠 My Take (Subjective, as the Author)
I believe we are entering a dangerous inflection point in digital life. Breaches are no longer anomalies — they’re systemic friction in the fabric of modern systems. Here’s what I think, and what worries me:
-
Trust is eroding fast. When people read headlines like “bank drained,” “medical records exposed,” or “private messages leaked,” digital life becomes scarier. Many users will retreat, limiting participation in valuable services, or demanding much higher standards.
-
Big firms are not safe. Even large enterprises with substantial security budgets are falling victim (see Allianz, Salesforce, Collins Aerospace). Security can no longer be a “luxury add-on” — it must be baked in from the start.
-
Attack vectors are diversifying. It’s no longer just about finding software vulnerabilities. Social engineering, supply chain weaknesses, misconfigurations, token abuse, and lateral SaaS exploitation are taking center stage.
-
Regulation is lagging. Laws like GDPR help, but enforcement is inconsistent and cross-border coordination is weak. I expect pressure for more aggressive rules: mandated cyber audits, required “data breach insurance,” greater corporate liability, even personal accountability for C-levels.
-
I foresee a “trust premium” economy. Companies that can credibly promise, demonstrate, and audit strong data stewardship — with real transparency — will gain a competitive edge. Users will begin to prefer services with provable security and liability. Those that don’t will be punished, either legally or in the market.
-
But there’s a dark path, too. If we overreact, we might see surveillance creep: governments demanding encryption backdoors, over-broad data retention laws, or forced compliance that undermines privacy rather than protecting it. I worry about solutions that swing from “too little security” to “too much control.”
-
In short: breaches will keep happening. But negligence should not. The next decade will be defined by who can rebuild trust — not by who can avoid the next hack (because some will). The question becomes: will we build accountability, transparency, and honor into the systems — or hope nobody looks too closely?






